





Remember all that talk about Active Directory (AD) becoming obsolete a few years back? Seems those predictions were way off the mark!
As we celebrate 25 years since its 1999 preview release, AD remains the undisputed king of on-premises identity infrastructure in many organizations worldwide. That’s right, around 90% of the world’s biggest companies (Global Fortune 1000) still rely on AD for their identity management needs.
Certainly, cloud-based identity services have become prominent, causing AD to take on a more supporting role as an intermediate identity (having certain responsibilities delegated to other platforms). However, this has not hindered AD from continuing to exist – and even flourish! Microsoft’s continual efforts to enhance AD’s capacity, efficiency, and protection showcase their dedication to its longevity.
This 25th anniversary is a perfect time to take a trip down memory lane. So let’s explore the history and evolution of AD, and delve into its pivotal role in shaping IT infrastructures worldwide.
Active Directory (AD) is a cornerstone of modern IT infrastructure, but its journey to dominance was anything but straightforward. Let’s take a trip back in time:
The story begins in the late 1980s at 3Com, where the foundational elements of AD were born. Originally an ambitious X.500-like directory service, it was short-lived. By 1990, 3Com exited the network software market, transferring the code to Microsoft.
Microsoft envisioned incorporating this directory service into LAN Manager 3.0. They planned to port it to a new database and build a user-friendly interface. However, a leadership change led to the cancellation of this project in favor of a completely new vision: the Cairo project. This ambitious idea aimed for a directory service outside X.500 standards, integrated with a new file system.
Unfortunately, the Cairo project was shelved in 1995, leaving Microsoft without a directory service for Windows 2000. In a surprising turn, developers from the Exchange Directory Service team quickly filled the gap. They adapted their existing codebase, heavily modifying it with new features. This marked the birth of what we know today as Active Directory.
It’s important to note that AD wasn’t a direct descendant of Novell NDS, Banyan StreetTalk, or even the Cairo project. It was a unique creation, informed by past endeavors and competitor insights. Additionally, while AD later supported LDAP, its development was separate from Exchange’s LDAP efforts.
At the time, Microsoft faced competition from established players like Novell’s NetWare and NDS, offering mature multi-platform directory services. LDAP-based solutions presented standards-based alternatives. Large players like IBM and Oracle also offered enterprise-grade directory services.
Despite the competition, AD carved out its niche by tightly integrating with the widely adopted Windows server environment. It offered centralized management, scalability, and policy management specifically designed for Microsoft-centric IT infrastructures. This successful integration of technologies, alongside strategic pivots, propelled AD from its 3Com roots to become an indispensable part of Microsoft’s product suite.
Active Directory (AD) wasn’t just a new technology; it was a game-changer. In its early days, it transformed how organizations managed their IT ecosystems. Domain controllers, organizational units, and Group Policy Objects gave IT administrators unprecedented control over their networks and resources.
First previewed in 1999 and officially released with Windows Server 2000, AD offered a major leap forward from traditional domain services. Its “multi-master model” allowed updates and changes to directory functionalities across any domain controller within a domain. This flexibility was a key differentiator.
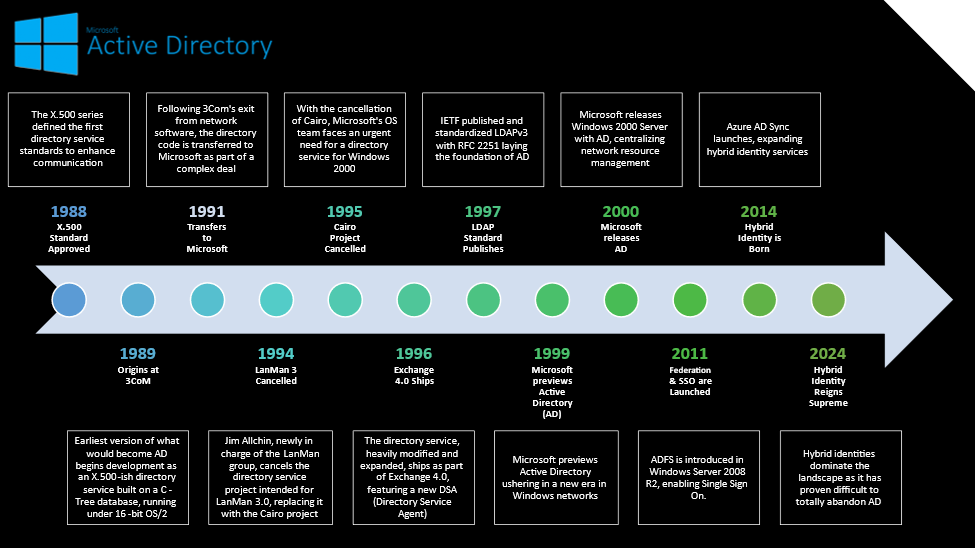
The underlying technology, LDAP (Lightweight Directory Access Protocol), might surprise some. It wasn’t a Microsoft invention. Developed in the early 1990s, it built upon the X.500 standards established by ITU-T in 1988, showcasing the deep roots and long-standing evolution of the technologies that led to AD.
Over the years, AD has continuously evolved, with each new Windows Server release adding new features and simplifying administration. While development briefly shifted towards cloud initiatives, Microsoft recently reaffirmed its commitment to AD. Recognizing its critical role in modern identity management, they’ve released updates focused on security, stability, and performance, addressing customer concerns and longstanding issues.
Active Directory (AD) has come a long way in its 25 years. It’s a story of resilience, adaptation, and constant change. While we celebrate its achievements, we can’t ignore the challenges.
Major security breaches have exposed AD’s vulnerabilities, highlighting the need for stronger defenses. Complexity, maintenance burdens, a shrinking pool of skilled professionals, and the cloud’s rise all pose difficulties for AD-reliant organizations.
Despite these challenges, AD remains a crucial component of identity infrastructure. However, its future hinges on overcoming these hurdles and adapting to changing trends. The shift towards Decentralized Identity (DCI) may necessitate substantial changes to AD’s architecture, or it may render it obsolete. The emergence of passwordless authentication could relegate AD to a role as a facilitator of on-premises authentication rather than a source of innovation.
Microsoft’s recent investments in security, performance, and scalability demonstrate a commitment to AD’s near future. However, experts predict AD’s relevance will likely last another decade, with a caveat: maintaining the current AD is unsustainable.
As Microsoft’s Alex Weinert puts it, “AD is where we are being attacked.” Weak configurations and neglect make AD an easy target. Moving forward, Microsoft needs to address vulnerabilities like Kerberos and NTLM, and provide a clearer roadmap.
Digital transformation highlights the importance of identity management. While AD’s future might see a lighter version, the need for on-premises authentication remains. High-security environments in government and research can’t fully rely on cloud-based models.
Organizations need a clear picture of AD’s future to plan effectively. Phasing out AD would require a significant transition effort.
We want to thank the numerous people who have played a part in the development, growth and long-lasting impact of Active Directory.
Happy 25th Birthday, Active Directory!
